Understanding Cyber Attacks in Healthcare

In the digital age, healthcare practices and senior care organizations are increasingly reliant on technology for patient records, treatment plans, and communication. This digital transformation, while beneficial, also opens the door to cyber threats. Protecting patient and resident data is not just about compliance with regulations; it is about maintaining the trust and safety of those who rely on healthcare providers for their well-being. A single breach can compromise sensitive information, leading to identity theft, financial loss, and severe disruptions in patient and resident care.
Cybersecurity in healthcare is paramount because of the high stakes involved. Medical records contain a wealth of personal information that, if accessed by malicious actors, can be exploited for various criminal activities. Moreover, cyber-attacks can disrupt operations, delay treatments, and even endanger lives. As cyber threats evolve in sophistication, healthcare providers must stay ahead with robust security measures to protect their systems and, ultimately, their patients.
If you’re not confident in your organization’s cybersecurity defense, click here to sign up for a FREE posture review! DAS Health cybersecurity experts will run an analysis on your defenses to ensure your safe.
What Exactly is a Cyber Attack?
Cyber-attacks are unauthorized attempts to access, steal, alter, or destroy data or disrupt services. In the context of healthcare, these attacks can have dire consequences, from compromising patient confidentiality to disrupting critical medical services.
Types of Cyber Attacks
Ransomware: This malicious software encrypts patient data, demanding a ransom payment to restore access. Healthcare providers face the dilemma of paying the ransom or losing access to crucial patient information.
Phishing: Deceptive emails targeting healthcare staff aim to steal credentials or deploy malware. These emails often appear legitimate, tricking even the most vigilant employees.
Distributed Denial of Service (DDoS): These attacks overload systems, causing service outages. In healthcare, this can delay patient care and disrupt hospital operations.
Insider Threats: Sometimes, the threat comes from within. Employees misusing their access to steal or compromise data pose a significant risk.
Medical Device Exploits: As more medical devices connect to networks, they become targets for cyber attacks, potentially compromising patient safety.
Why is Healthcare a Target?
Critical Nature: Attackers deploying ransomware aim to get paid, exploiting the urgency in healthcare services to prompt quick ransom payments due to the potential risk to lives during service outages.
Soft Target & Easy Entry: Vulnerabilities in medical devices, often difficult or impossible to patch, leave healthcare organizations exposed to attacks, allowing cybercriminals to access and move laterally within networks.
Lack of Resources, Awareness, and Expertise: Healthcare providers often face constraints that limit their ability to invest in cybersecurity tools, processes, personnel, and user education, as cybersecurity is not their primary focus.
Broad Attack Surface: The range of devices and environments, including on-premises and remote users, expands the attack surface for cybercriminals, with remote access introducing additional risks and vulnerabilities.
Value of Data: Healthcare organizations possess vast amounts of sensitive data, including medical histories, Social Security numbers, and financial information, which attackers can easily use and resell.
The Unrelenting Frequency of Healthcare Cyber Attacks
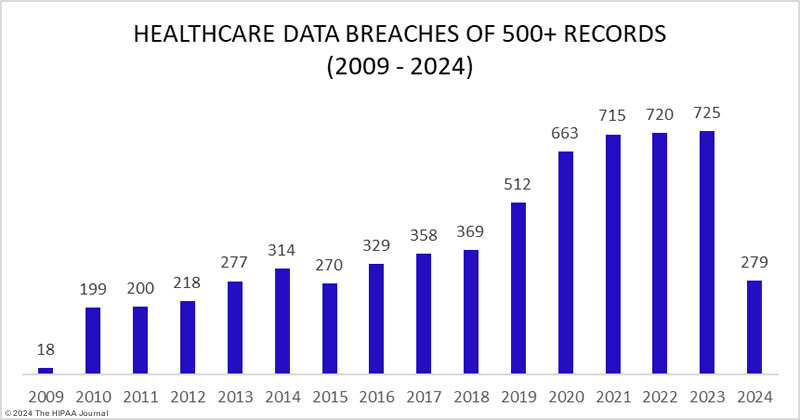
Between 2009 and 2023, a staggering 5,887 healthcare data breaches of 500 or more records were reported to the Office for Civil Rights (OCR). These breaches exposed over 519 million healthcare records, surpassing the population of the United States.
In 2018, healthcare data breaches of 500 or more records were reported at a rate of around one per day. By 2023, this rate had more than doubled, with an average of 1.99 breaches reported daily, exposing approximately 364,571 healthcare records each day.
2024: A Year of Noteworthy Cyber Attacks
Change Healthcare
- Impact: Significant delays in patient care and reimbursement.
- Downtime: 3+ months.
- Cost: Expected to exceed $1 billion.
- Reason: Lack of Multi-Factor Authentication (MFA).
Ascension
- Impact: 140+ locations forced to use paper charts.
- Downtime: 4+ weeks.
Lurie Children’s Hospital
- Impact: 240,000+ pediatric patients affected.
- Downtime: 3.5 months.
Recognizing the Signs of a Cyber Attack
Healthcare organizations must be vigilant and recognize the indicators of a potential cyber attack:
- Suspicious Emails or Messages: Be wary of unexpected or unusual communications.
- Unusual System Behavior: Slower performance or unexpected crashes can signal an attack.
- Unauthorized Access Attempts: Frequent or unusual login attempts should be investigated.
- Altered or Missing Data: Changes to or loss of data can indicate a breach.
- Network Anomalies: Unusual traffic patterns could signify a DDoS attack.
- Security Alerts and Logs: Pay attention to alerts from security systems.
- Ransom Notes or Demands: Clear indicators of a ransomware attack.
- Unexpected Software Installations: New, unauthorized software can be a sign of malware.
What to Do After a Cyber Attack: The Road to Recovery
The best defense is a good offense. Preparing an Incident Response Plan (IRP) before a breach occurs is crucial. Any suspicious activity or suspected security issues should be reported to your security team immediately.
An effective IRP includes detailed steps based on the type and severity of the incident. Key areas covered should include:
- Preparation: Establishing and training a response team.
- Detection and Analysis: Identifying and understanding the attack.
- Containment: Limiting the spread of the attack.
- Eradication: Removing the threat from your systems.
- Recovery: Restoring and validating system functionality.
- Post-Incident Activity: Reviewing and improving response strategies.
Stay Ahead of Cyber Threats with DAS Health
At DAS Health, we specialize in providing comprehensive cybersecurity services tailored for the healthcare sector. Our expertise helps you safeguard patient data, maintain compliance, and ensure the smooth operation of your healthcare services. Don’t wait for an attack to strike—partner with DAS Health to fortify your defenses and secure your future.
